On 9th of January, 2019, Intigriti announced following CTF challenge
( https://twitter.com/intigriti/status/1082979668972748803 ). As I recently started trying out CTFs,
I thought to give it a try, although my CSSLP exam was almost close.

So where to start? As there was no other hints at that time, and there is an emoji pointing to the
attached image, I thought the clues or flag itself was inside the image, so I downloaded it to my
Kali VM.

Then it was time to analyze the downloaded image file.

Using “strings” command on the image file showed some interesting texts like “lmao” and
“nottheflag.pdf”. So I thought maybe there was a pdf file embedded inside the image file (As I
remembered reading similar steganography techniques in twitter or somewhere before)
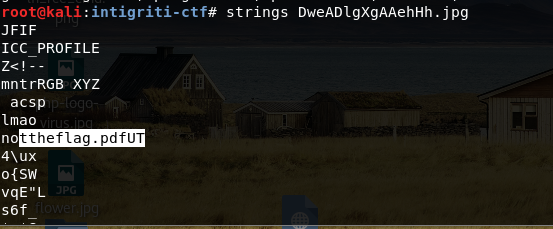
On the first attempt, I just renamed the file to .zip extension and used “unzip” command which
gave me the pdf file.
But then I found a better way to do that using “binwalk” command later thanks to further google
searches. This “binwalk” command shows what are the embedded files inside a file.
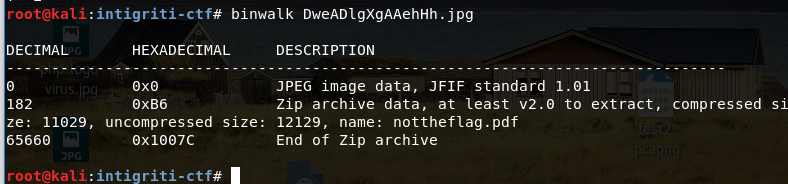
If you use “-e” option of “binwalk”, it even extracts those files to the current directory. But I was
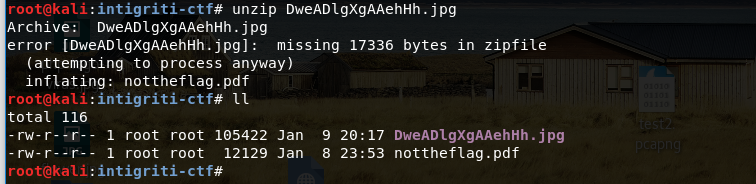
still new to this tool, so I only found about it later. I just used “unzip” command on the jpg, and
voilà, now there was a file named “nottheflag.pdf” in my current directory.
Opening the PDF file showed a base64 encoded string and a URL to a tweet.
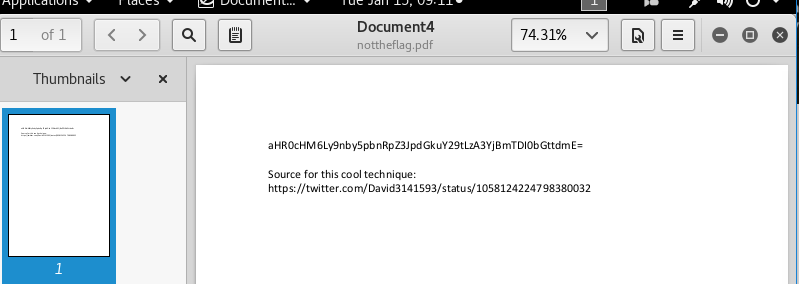
Decoding the base64 string:

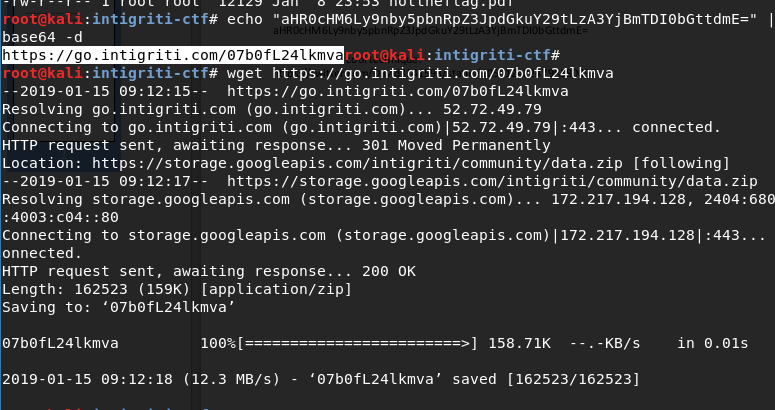
Accessing the decoded URL (https://go.intigriti.com/07b0fL24lkmva) pointed to a zip file.
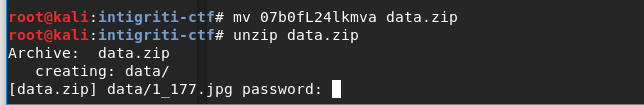
Ok, it is an encrypted file. Where is the password? Let's see what hints are posted by intigriti.

There is an emoji pointing up. I checked the original tweet again, and examined the cover image
of the current image, even found another twitter account named “WhereIsTheFlag”.
https://twitter.com/WhereIsTheFlag
Still I did not have a clue where was the password.
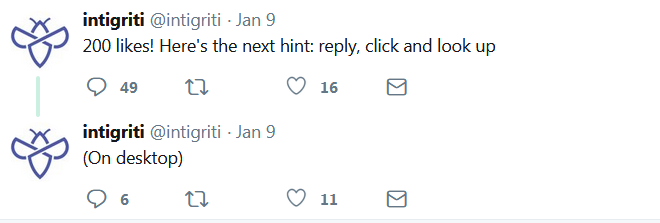
Again new hints were posted by intigriti pointing up.
Where is it?
Feeling same as @SYNTAXERRORBA
The ceiling? 😓

The sky? 😕

Ok, after sometime, I remembered I had to study for CSSLP exam. So gave up.
…….
But again later, Another hint.
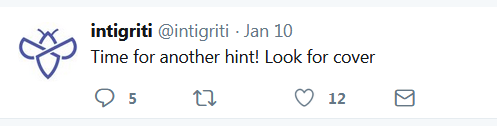
I already looked cover image of intigriti twitter account. (But I forgot to check the cover image of
other twitter account “WhereIsTheFlag”, that was where they hid the password according to
another writeup). So no password for me.

Another hint is about a matrix. The MATRIX?

😕, maybe they are talking about a color table in JPG file?
Spent more time wasting about reading about JPG and using commands like xxd to analyze jpg
file. Then I remembered again I had to study for CSSLP and went back to studying.
The last hint.
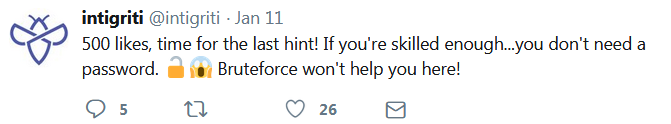
I am not skilled enough on CTFs yet, but I can try.
Using unzip commands to see available data on the zip file:


unzip -l command shows encrypted zip file contain 441 jpg image files with two different sizes
(314 and 317/318 bytes)
as the last hint says we do not need to decrypt the zip file, I thought image filenames and file
sizes should be sufficient to get the flag.

As one of the hint is about a matrix, it is possible the information from files should be arranged in
a matrix and because 441 is 21x21, this assumption seemed correct. Best known data
representation (at least for me) using a matrix is QR code. According to wikipedia article about
QR code, the version 1 of QR code is 21x21 which gives further credence to possible retrieval
of QR code using found data. If this assumption is correct, two image sizes may be used to
represent for black and white colors.
Therefore the next step was to convert the file sizes to 0/1 or black/white and then to arrange
those in 21x21 matrix ordered by file name.
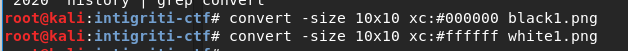
First I generated a black png and a white png with size 10x10 pixels for generating the main
image, using imagemagick convert command.
Then I generated an imagemagick convert command which arranges above created black and
white images in rows and columns, while black representing image files greater than 314 bytes,
and white representing image files equals to 314 bytes in size.
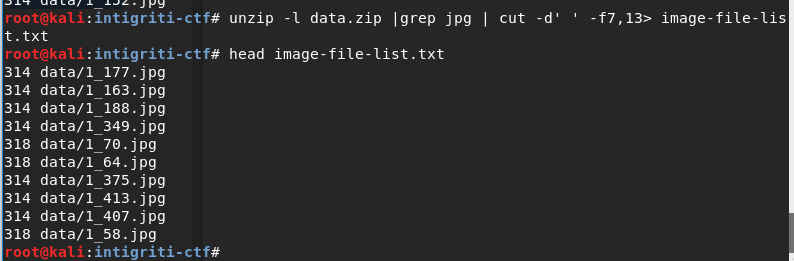

Then I copied the generated imagemagick command from qr2.txt and executed it in command
line (somehow using `cat qr2.txt` did not work, so had to copy paste using xclip command).

Now it is time to see the generated image. ⏳
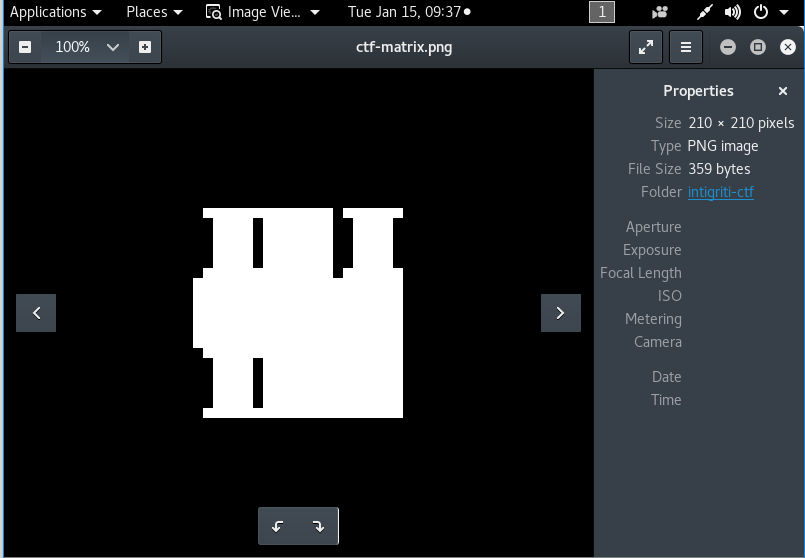
So I got a silhouette of a nice building. 😯 I don’t think that is the flag.
Then after sometime, as the last attempt, I thought maybe if I compared the encrypted file
content (retrieved through zipdetails command), I could find which files were similar (black or
white). But It did not work as I did not find any encrypted file with same data as any other file.
Then I gave up for the last time as I still had another high priority, CSSLP exam. So no flag for
me this time, but at least I passed (provisionally) CSSLP exam 😊.
You can find a writeup on a successful attempt to capture this flag by @DJBusyR
here https://busyr.com/writeups/intigriti_-_find_the_flag_earn_swag.pdf
( https://twitter.com/intigriti/status/1082979668972748803 ). As I recently started trying out CTFs,
I thought to give it a try, although my CSSLP exam was almost close.
So where to start? As there was no other hints at that time, and there is an emoji pointing to the
attached image, I thought the clues or flag itself was inside the image, so I downloaded it to my
Kali VM.
Then it was time to analyze the downloaded image file.
Using “strings” command on the image file showed some interesting texts like “lmao” and
“nottheflag.pdf”. So I thought maybe there was a pdf file embedded inside the image file (As I
remembered reading similar steganography techniques in twitter or somewhere before)
On the first attempt, I just renamed the file to .zip extension and used “unzip” command which
gave me the pdf file.
But then I found a better way to do that using “binwalk” command later thanks to further google
searches. This “binwalk” command shows what are the embedded files inside a file.
If you use “-e” option of “binwalk”, it even extracts those files to the current directory. But I was
still new to this tool, so I only found about it later. I just used “unzip” command on the jpg, and
voilà, now there was a file named “nottheflag.pdf” in my current directory.
Opening the PDF file showed a base64 encoded string and a URL to a tweet.
Decoding the base64 string:
Accessing the decoded URL (https://go.intigriti.com/07b0fL24lkmva) pointed to a zip file.
Ok, it is an encrypted file. Where is the password? Let's see what hints are posted by intigriti.
There is an emoji pointing up. I checked the original tweet again, and examined the cover image
of the current image, even found another twitter account named “WhereIsTheFlag”.
https://twitter.com/WhereIsTheFlag
Still I did not have a clue where was the password.
Again new hints were posted by intigriti pointing up.
Where is it?
Feeling same as @SYNTAXERRORBA
The ceiling? 😓
The sky? 😕
Ok, after sometime, I remembered I had to study for CSSLP exam. So gave up.
…….
But again later, Another hint.
I already looked cover image of intigriti twitter account. (But I forgot to check the cover image of
other twitter account “WhereIsTheFlag”, that was where they hid the password according to
another writeup). So no password for me.
Another hint is about a matrix. The MATRIX?
😕, maybe they are talking about a color table in JPG file?
Spent more time wasting about reading about JPG and using commands like xxd to analyze jpg
file. Then I remembered again I had to study for CSSLP and went back to studying.
The last hint.
I am not skilled enough on CTFs yet, but I can try.
Using unzip commands to see available data on the zip file:
unzip -l command shows encrypted zip file contain 441 jpg image files with two different sizes
(314 and 317/318 bytes)
as the last hint says we do not need to decrypt the zip file, I thought image filenames and file
sizes should be sufficient to get the flag.
As one of the hint is about a matrix, it is possible the information from files should be arranged in
a matrix and because 441 is 21x21, this assumption seemed correct. Best known data
representation (at least for me) using a matrix is QR code. According to wikipedia article about
QR code, the version 1 of QR code is 21x21 which gives further credence to possible retrieval
of QR code using found data. If this assumption is correct, two image sizes may be used to
represent for black and white colors.
Therefore the next step was to convert the file sizes to 0/1 or black/white and then to arrange
those in 21x21 matrix ordered by file name.
First I generated a black png and a white png with size 10x10 pixels for generating the main
image, using imagemagick convert command.
Then I generated an imagemagick convert command which arranges above created black and
white images in rows and columns, while black representing image files greater than 314 bytes,
and white representing image files equals to 314 bytes in size.
Then I copied the generated imagemagick command from qr2.txt and executed it in command
line (somehow using `cat qr2.txt` did not work, so had to copy paste using xclip command).
Now it is time to see the generated image. ⏳
So I got a silhouette of a nice building. 😯 I don’t think that is the flag.
Then after sometime, as the last attempt, I thought maybe if I compared the encrypted file
content (retrieved through zipdetails command), I could find which files were similar (black or
white). But It did not work as I did not find any encrypted file with same data as any other file.
Then I gave up for the last time as I still had another high priority, CSSLP exam. So no flag for
me this time, but at least I passed (provisionally) CSSLP exam 😊.
You can find a writeup on a successful attempt to capture this flag by @DJBusyR
here https://busyr.com/writeups/intigriti_-_find_the_flag_earn_swag.pdf
No comments:
Post a Comment